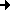| • |
You transfer all packets to your ISP's mail server, which then sends them to the entry remailer(s).
| • |
Deactivate the 'Use Anon Mail Host' checkbox at the 'Anon' tab in order to use the mail server configured at
the 'Mail S' tab. |
| • |
Enter the access data of your ISP at the 'Mail S' tab. |
|
|
| • |
If you don't like to involve your ISP in anonymous transmissions, then send remailer data through an alternative
mail server (maybe an anonymously created freemailer account) or directly to the SMTP port of a single entry remailer.
| • |
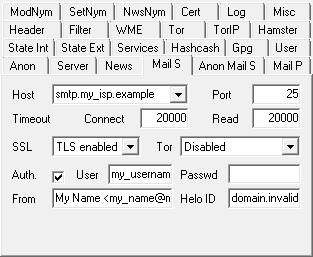
Activate the 'Use Anon Mail Host' checkbox at the 'Anon' tab in order to use the mail server(s) configured
at the 'Anon Mail S' tab. |
| • |
At the 'Anon Mail S' > 'Anon' tab enter the communication parameters of the mail servers you intend to
use for anonymous messages. You can either specify mail hosts that aren't restricted to specific mail
addresses (e.g. the one of your ISP or a freemailer) or ones that are only run to supply their own remailer.
The 'Mx Relays' tab holds a list of remailers, which offer such a service, and their access data. For
mail servers associated to a single remailer you have to set the remailer name and specify how to modify the
remailer chain accordingly (by replacing the existing entry remailer or prepending it as another one). |
| • |
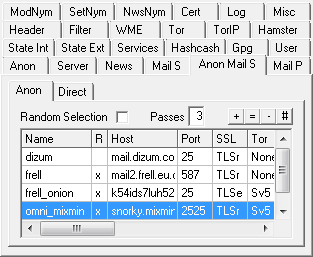
If 'Random Selection' is checked instead of using the server selected within the list the mail hosts for
delivery are randomly chosen from those list entries for which 'Random' is activated. With more than 4
remaining delivery attempts only a portion of the unsent chunks (1/(passes-3), which means with 8
remaining passes 1/5 = 20%) is chosen to be sent to a single SMTP host to increase redundancy. |
| • |
An encrypted communication and the usage of Tor would further increase your security. Information about
'Hidden Services' and how to set up Tor can be found in the 'Tor' section of this manual. |
|
|
| • |
Finally there's a way to forward packets directly to the remailer network but avoid the dependence on one single entry
remailer. In this case OmniMix tries to find the remailer-associated mail host for each packet by itself. If an
unintermediate transfer to the remailer fails, either because its mail host can't be found or rejects the message, the
packet finally is sent to it through an unrestricted mail server.
| • |
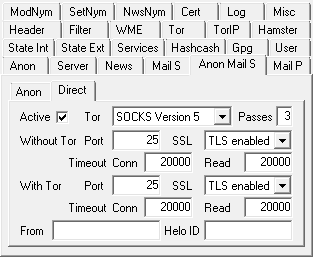
Activate the 'Use Anon Mail Host' checkbox at the 'Anon' tab in order to use the mail server(s) configured
at the 'Anon Mail S' tab. |
| • |
Activate direct delivery at the 'Anon Mail S' > 'Direct' tab. |
| • |
Select an unrestricted, not remailer-associated mail server from the list of anonymous mail hosts
('Anon Mail S' > 'Anon' tab) as a fallback option in case direct delivery of the actual chunk isn't possible. |
| • |
For a direct package delivery to the entry remailer OmniMix first has to figure out the associated mail
host(s) (by a DNS MX record lookup). Problems arise when for anonymity reasons all traffic has to be routed
through Tor. As Tor itself neither provides such a lookup service by itself nor supports the UDP protocol,
the standard for DNS requests, OmniMix is compelled to strictly use the TCP protocol to contact DNS servers,
which however not all of them allow. That's why TCP compatible name servers, like those run by
OpenNIC have to be entered into the 'Name Servers'
list ('Services' > 'DNS' tab), used by OmniMix for that purpose. |
|